tip
Sign your commits with GPG and prove your identity
GIT is one, if not the most, major tool many of us use every day at work or for their open source projects.
When working with it, it often comes naturally that it properly associates name and e-mail (your identity) with commits you do.
What sometimes may get lost though is, that it's super simple to just spoof somebody else's identify and push commits with a different name and e-mail.
git uses the information as specified in your ~/.gitconfig to set the author of a commit
[user]
name = Mike Penz
email = [email protected]
To offer users a form to verify their identity GitHub, GitLab and other services offer users to sign their commits using a GPG key.
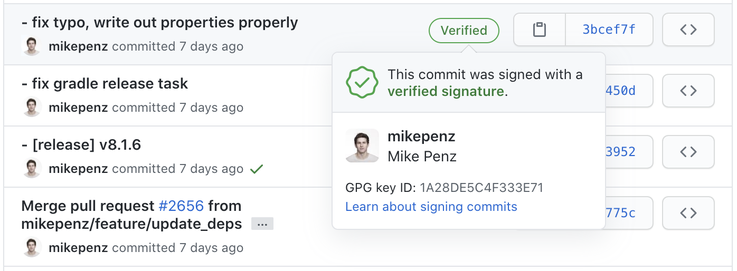
Users will upload their public key, and use their private key to sign the commit, and GitHub for example will then show a verified badge on those commits which will inform other users that this commit comes from a trusted source.
Getting Started
To get started you will need GPG on your computer to create a new key pair.
Usually I go with the GPG Suite, which offers a nice UI to manage your keys. (You may want to use advanced installation to only install the parts you need)
But you can also use any other solution to create your key pair.
After installing GPG Suite (or your prefered solution) first create a new key.
Using GPG Suite, start the GPG Keychain, which shows all current known GPG keys on your system.
Click on New and you will be offered to enter your name, e-mail and password. Ensure to pick a secure password to protect your key.
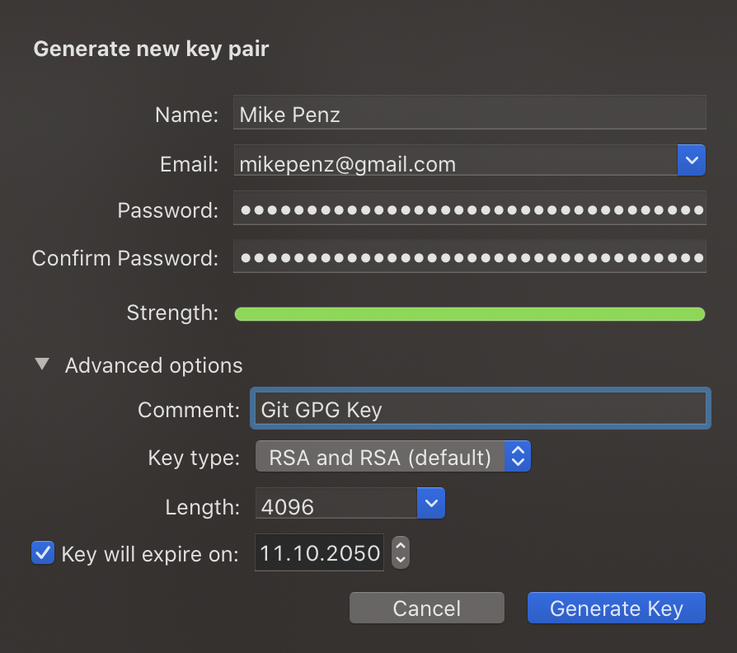
Usually I go with RSA and a length of 4096 for the best security of the key.
Complete the creation by clicking "Generate Key". This will create new private/public key pair you can use.

In the Key Details you will find the Key ID which we will need in a bit. But it also highlights all the different details of this key. Like your defined Name, E-mail and Comment. Also the date of creation and expire date.
Now after we created the key pair we want to configure git to use this key to sign commits.
Configure GIT
GIT natively supports using GPG keys to sign commits, for this we have to configure the ~/.gitconfig to automatically use the created key for commits.
First define the signingkey in the [user] section, and afterwards define to do gpgsign in the [commit] section.
[user]
name = Mike Penz
email = [email protected]
signingkey = 27E15D38
[commit]
gpgsign = true
This will automatically work if you use the git CLI or if you use Android Studio to commit and push to your repository.
To also sign tags using the git CLI provide the -s parameter. (git tag -s)
Sourcetree
When using source tree you will have to do 2 additional steps to configure the key. These steps are required per repository.
In the repository settings enable GPG key signing for commits.

After enabling GPG key signing in the settings you will be able to enable Sign commit from within the commit options.
This is required to be enabled, otherwise sourcetree won't sign the commit.

Configure GitHub / GitLab
After configuring our local environment, the last part is to configure GitHub or GitLab to be able to identify and verify the signature of commits.
For this we require the public key of our pair.
Open the GPG Keychain, and right click on the key created to sign commits.
Choose the Export option, which will offer to save a file named similar to Mike Penz (27E15D38).asc
Save it, and use your preferred editor to open it, and copy its contents.
It will look something like this (Shortened for this post).
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQINBF+DEhMBEAC9Vtpub9CHYVAaspfdcWQ5Tijkz3mhJig337V1gV9REt6p40LS
mqKDTyW8x5ZYly5RZqujOIVLy/k9eoTFal+U8Kio+rlEamYnAMTXGx3WyxzbT1bA
zv82SLQ5tdJ4qnbdFo74QLWLFAkcQo/+dOzitnptxtY4V95+yMIawH1xp4T6Gp5Q
QT95FpYaRruX4pCu13H662KkxrZ7Fv26tuqDpTFLDeIhickYFA==
=Dklm
-----END PGP PUBLIC KEY BLOCK-----
GitHub
Head over to your GitHub settings and find the SSH and GPG keys options.
Click New GPG Key

Paste the public key we opened in our preferred editor in the previous step. And save by clicking Save GPG Key.
If you create a new change to your project and commit it, GitHub will show the verified batch after pushing the changes.
GitLab
Similar to GitHub, GitLab offers a settings page to add the GPG Key too. Open your settings and open GPG Keys.
It will offer you a quick UI to paste the public into, to add it to your account.

After pressing Add Key you are done.
If you create a new change to your project now, and commit the these changes. Then push the changes. GitLab will show that your commit is now verified too.
Feedback
Do you have more suggestions to improve the security of commits, or have additional tips, thoughts, feedback, improvements or comments?
Let me know @mike_penz